As the number of IoT devices being integrated into our businesses and lives increase, more decisions are made on the data they produce. For informed decisions to be made, we need to trust the data. This relies on having trusted devices. Building trust into devices is increasingly difficult, as IoT devices are growing in complexity – containing more code and hardware that will inevitably contain security vulnerabilities.
By 2025 there will be around 75.44 billion connected devices, producing huge amounts of data that cloud services will use to make decisions. A hardware-based Root of Trust (RoT) is crucial if we are to trust the devices providing this information. The RoT can provide some basic security functions, such as crypto functions and secure storage that help to protect the device against common hacks. Attestation is another one of these functions, helping to ensure that the cloud-based software knows who it is talking to and builds the chain of trust from the chip’s RoT to the relying party. In this blog we look at:
- What device attestation is and why it’s important
- Introduction to Entity Attestation Tokens and the role of relying parties
- How device attestation can help device manufacturers
- A simplified way to implement device attestation
What is Device Attestation?
Device attestation can be defined as the mechanism enabling a device to make claims about its status that can be useful to manufacturers and cloud service providers who want assurance that they can trust the devices. The claims include a device ID, the software version, and the hardware version, and is provided in a manner that can be verified externally. A relying party will process the attestation result to make policy decisions, such as whether to grant a device access to certain resources.

Why is Device Attestation Important?
As the number of IoT devices increases, so do concerns around the number of devices connecting to a network. More devices create more management and more security risks. Attestation enables the easy identification of specific properties, that helps identify devices that may have been tampered with or have outdated software. Having this assurance builds trust in your devices and the integrity of your network, allowing you to make informed decisions based on a reliable source.
What is an Entity Attestation Token?
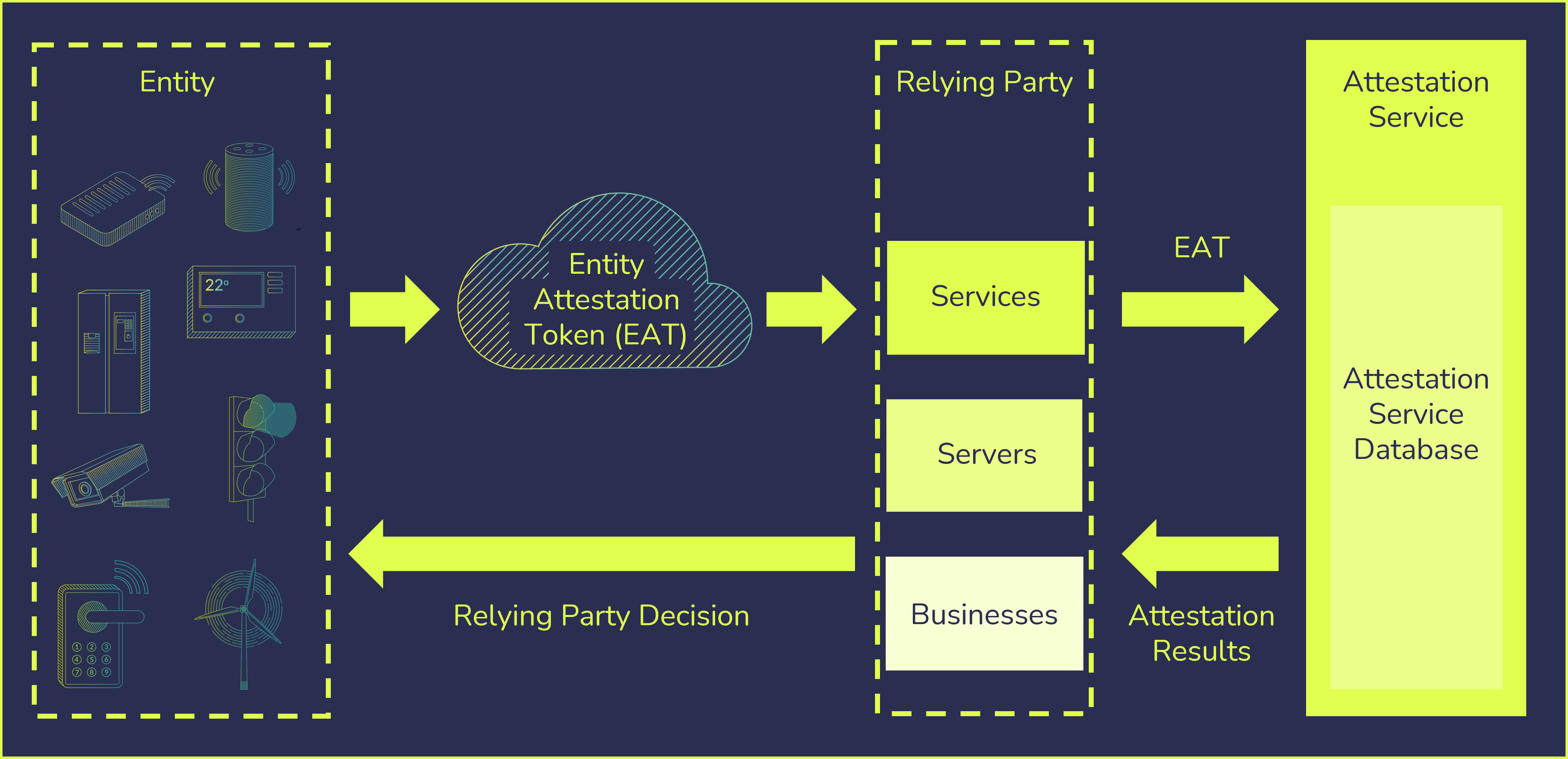
An Entity Attestation Token, otherwise referred to as EAT, is a small blob of data that is cryptographically signed. An EAT token is encoded in either one of two standardized data formats: a compact binary format (CBOR) or in the text-based format JSON. A digital signature is then used to protect its content. The technical specification defining the content of the EAT token, which are claims about the hardware and the software running on a device, is specified by the Internet Engineering Task Force (IETF). Entity attestation tokens help to create trust between a device and a cloud application that may be managing the device. The service that makes decisions based on the EAT is called the ‘relying party’.
What is a Relying Party?
In a standard scenario, an IoT device provides an attestation token for a server or service so that it can securely know the characteristics of that device. This server or service is known as the relying party. They receive the EAT token and can verify the claims with the manufacturer, or a trusted third party (a verifier). This enables the process of enrolling a new device onto a network to be automated and helps with counterfeit detection and management of updates. The relying party is the end consumer of the attestation result and has the power to decide whether or not to trust the device.
How Does Device Attestation Work?
Cloud service providers need to make informed judgements on end devices to ensure the data they are providing can be trusted. EAT has the capabilities to provide this source of trust, using a cryptographically signed piece of data containing claims that are generated in the device RoT. There are many ways it can be useful, but most importantly it can be read by the relying party. The relying party can verify the claims made by the device such as:
- The unique identity of the device
- Installed software on the device and its integrity status
- Security assurance and certification status
- Manufacturer of the device hardware
Using this information, the relying party can make informed decisions such as whether the device is legitimate and should be onboarded, or what services should be enabled based on its security credentials.
Access the Entity Attestation Token White Paper
Learn more about entity attestation tokens and how to implement them to communicate trust
Why is Attestation a PSA Certified Security Goal?
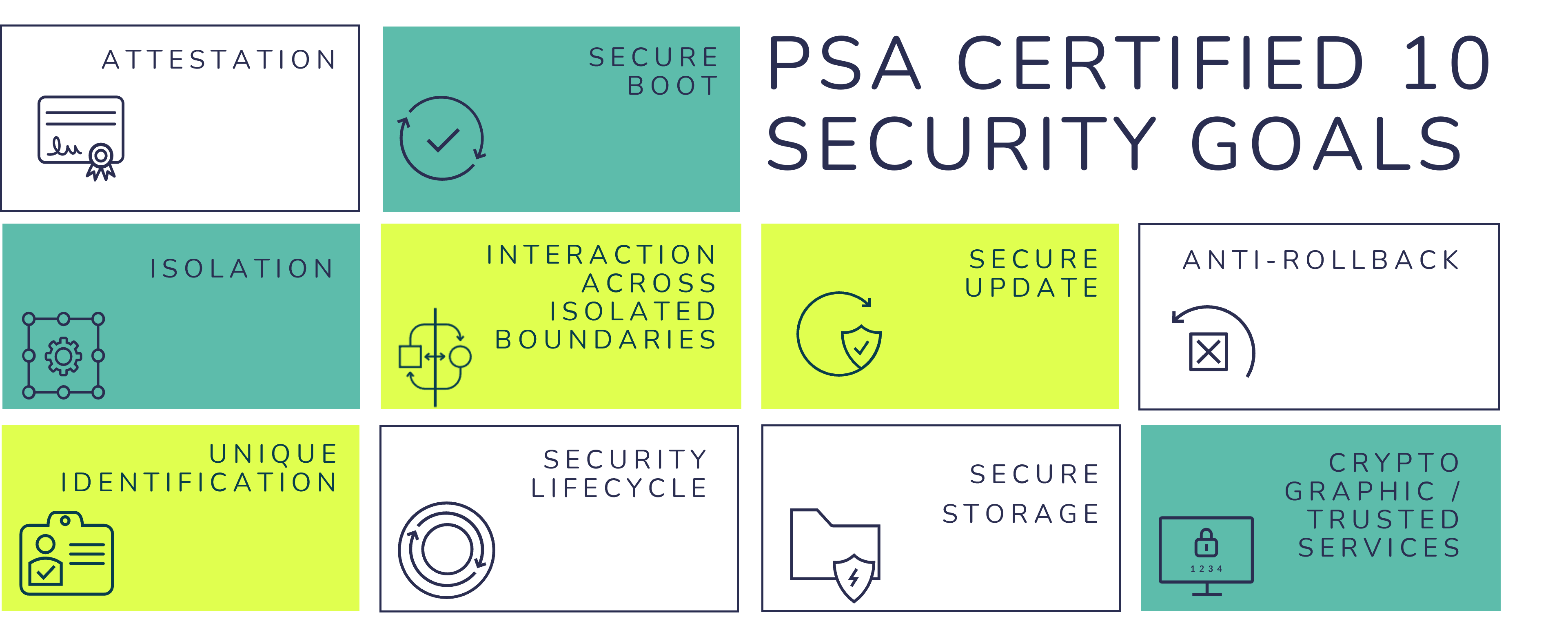
PSA Certified outlines the high-level 10 security goals to help guide security best practice in IoT devices, these are outlined in the Platform Security Model. Developed by industry leading security experts, the 10 security goals are a key aspect of the PSA Certified framework and provide a foundation of security that you can build your device on. Although each device has unique security requirements, the 10 security goals highlight functionalities that should be implemented into every connected device. The third of these goals is aimed at ensuring all devices are securely attestable as it’s crucial that the trustworthiness of a device can be established. This includes proving the identity and security state of a device through attestation.
If we are to realize the potential of digital transformation on the scale of a trillion devices, we first need to be able to manage and support these devices in the field, this is where the value of attestation can really be felt. To manage and support devices remotely manufacturers or service providers first need to be able to verify the device. To do this, devices are enrolled with a device verification system that includes attestation. As the number of IoT devices continues to scale, attestation verification services are increasingly expected to be deployed by manufacturers or service providers, highlighting the need for an accessible approach with standardized implementations.
PSA Functional APIs and Entity Attestation Tokens
PSA Certified calls for a small hardware protected region of the chip, called the PSA Root of Trust (PSA-RoT), that acts as a source of confidentiality and integrity. The PSA-RoT includes a small set of useful security functions, that are made accessible to software developers via open source and easy-to-use PSA Functional APIs. Those APIs have been specifically designed to facilitate usage of security functions and avoid most of the common errors encountered while developing firmware. One of these key APIs deals with attestation and the creation of an Entity Attestation Token.
How Can Companies Implement Attestation?
Many chip providers are building in a PSA-RoT using open-source firmware from Trusted Firmware. This open-source reference implementation includes an attestation service, which includes an EAT library. OEMs, when building a device, can use include the PSA trusted services in their software stack and to use the PSA Functional APIs, and the PSA Attestation API in particular, to enable devices to expose EAT tokens.
What is required:
- The chip or device will also need a private attestation key for signing the tokens.
- The device manufacturer will need either an in-house or third-party cloud side verification service.
- The relaying party will need a small library on the cloud side to receive and process EAT tokens.
OEMs can find out which chips support EAT by looking for PSA Certified chips in the certified products catalogue that have passed the PSA Functional API test suite that includes the EAT API.
Easing the Implementation of Entity Attestation Tokens
PSA Certified aims to reduce IoT fragmentation and ease security concerns across the ecosystem. This includes providing free, editable resources to help guide the design and implementation of specific security functions. The Entity Attestation Token whitepaper was co-created with the author of the popular EAT open-source project t_cose and provides a unique insight into the technology, exploring the anatomy of an Entity Attestation Token, the four-step process of device attestation and how the PSA Certified ecosystem is supporting its adoption.
Next Steps
Access the free white paper now to learn more about Entity Attestation Tokens, use cases and how to implement them.

