IoT Security in the 2010’s – “The Wild West Years”
Businesses, consumers and governments recognise that IoT insecurity is a problem, and this is backed up by the number of news stories covering IoT devices being hacked. You may remember some of the most memorable hacks: the car that could be compromised and driven off the road, the connected video cameras that could be turned into a botnet to take out parts of the internet infrastructure, the casino fish tank that was used to spy on sensitive network data or the hacked tracking watches. When you dig into how these products were compromised, they all possessed common vulnerabilities that could have been avoided by applying good security principles.
Enter Platform Security Architecture (PSA)
Platform Security Architecture was first launched in 2017 to encourage the industry to design-in security rather than add it as an afterthought. PSA helps IoT developers by providing a holistic set of free resources to the electronics industry that have been methodically developed:
- Threat modelling of IoT devices to identify core common security requirements
- Generic security model with 10 goals
- Firmware architecture documentation
- Open source code, Trusted Firmware-M, for the PSA Root of Trust (PSA-RoT) with built-in security functions
The provision of an open source software reference implementation proved to be a critical step in gaining widespread adoption by chip vendors. Most of the world’s top 10 chip vendors have embraced PSA Certified and can now deliver a new security component, the PSA-RoT, with trusted boot, crypto, attestation and secure storage trusted functions. OEMs starting an IoT development with a PSA enabled chip today have a security component they can build on to deliver trusted devices and trusted data for cloud services.
PSA Certified: Moving the Industry from “Trust Me” to Independent Testing
Traditionally chip vendors, would have proprietary solutions for a chip’s Root of Trust (RoT) that might include features such as trusted boot and crypto accelerators. These solutions would not normally be security certified as there was no standard protection profile for IoT. The OEM would have to trust the vendor that they had done a good job, applied sound security principles and security engineering.
With PSA Certified we have created a standard security component, the PSA-RoT, made up of trusted hardware and trusted software that can be evaluated in a test lab. With this, an OEM developing IoT products can now have a standard benchmark for chip security that a test lab has evaluated, with access to the source code and knowledge of the hardware.
At the software platform or device application level the pragmatic approach is to show that the design is based on sound security principles. The code is usually considered too large to be exhaustively assessed for security vulnerabilities and tested. What is required is a small set of methodically derived security goals that are generally applicable to connected products.
To enable the transition to independent testing, the PSA Certified Founding Members agreed to create a security assessment scheme that works at IoT scale. We launched PSA Certified one year ago with the backing of the world’s major chip vendors, this momentum is a game changer in an otherwise fragmented market.
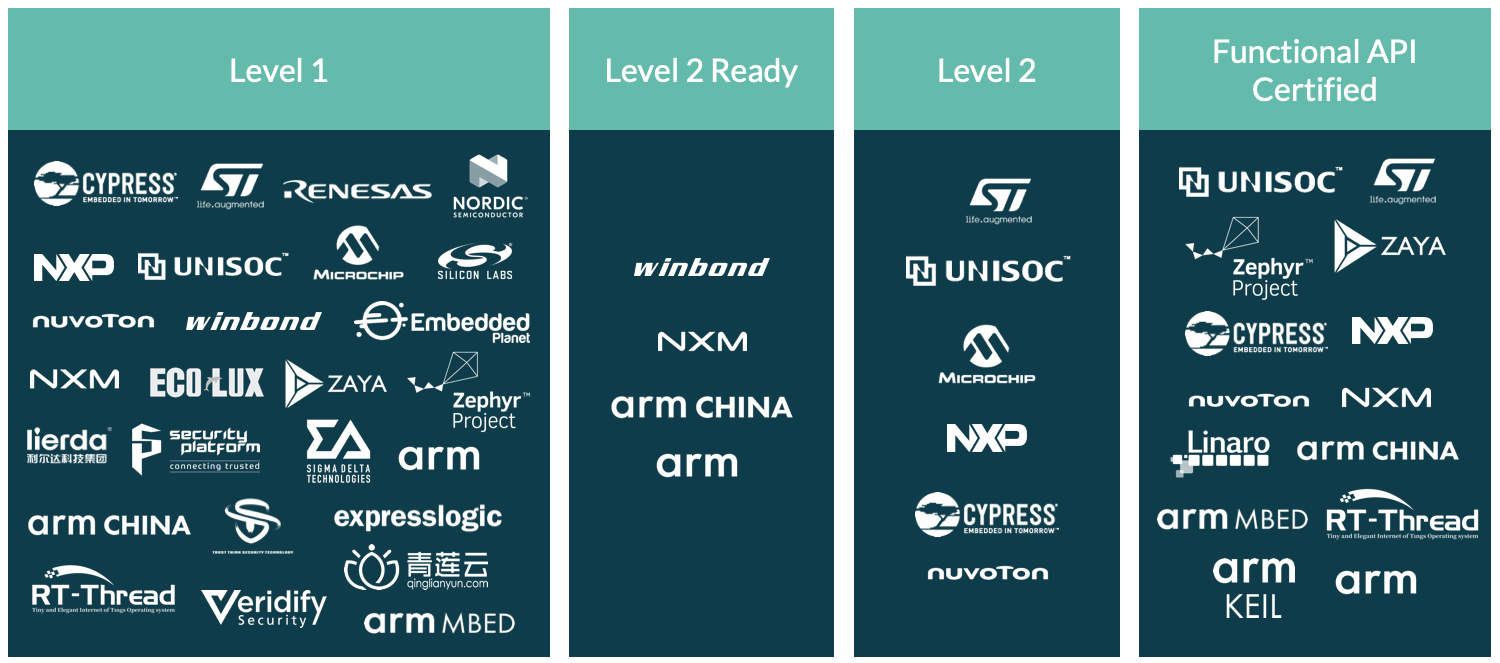
The scheme has three levels of increasing security assurance and robustness, designed for systems with a RoT in the chip at its foundation. PSA Certified Level 1 was created for the chip vendor, software platform and device developer, with a set of approximately 40 critical security questions that demonstrate how the developer applied good security principles and used a hardware-based PSA-RoT.
At the time of writing there are over 30 PSA Certified Level 1 products from chip companies, software platforms and device makers. PSA Certified Level 2 and Level 3 focus on the PSA-RoT from the chip vendor and offer progressively increasing levels of assurance and robustness.
PSA Certified enables a chip manufacturer, software platform or device maker to transition from saying “Trust me – I’ve applied good security principles” to one who can say “I took my product to a test lab and got it independently assessed and here is the evidence”. It is a major step forward in building trust, based on evidence, through the ecosystem.

A Growing Challenge – Fragmentation of Security Standards, Baseline Requirements and Law
A new and growing challenge in the IoT industry is the forest of new security standards, baseline requirements, frameworks and now regulations. This is bewildering for IoT developers, and choosing which IoT security standard, framework, baseline and principles to follow is a real issue. Add to this the regional differences where each major market adopts slightly different requirements and wording, the challenge to develop products for multiple markets worldwide becomes more complex and intimidating. If you are an IoT product manufacturer how do you navigate this and decide which IoT security framework to turn to?
Navigating Security Standards and Regulation in the 2020’s – PSA Certified Healing Fragmentation
At launch we promised to monitor the ecosystem and make any necessary changes to the scheme that further reduced fragmentation in the market. Which is why we’ve launched the 2020 update to the PSA Certified Level 1 questionnaire (officially known as v2.0).
In this version we have worked on aligning the security questions with the essential parts of four other documents:
- ETSI 303 645v2 (formerly security by design) which is likely to be important in the European market
- NISTIR 8259 baseline that is likely to be important to North America
- Californian state law (one of the first big markets with law requiring security features)
- Draft UK DCMS IoT requirements
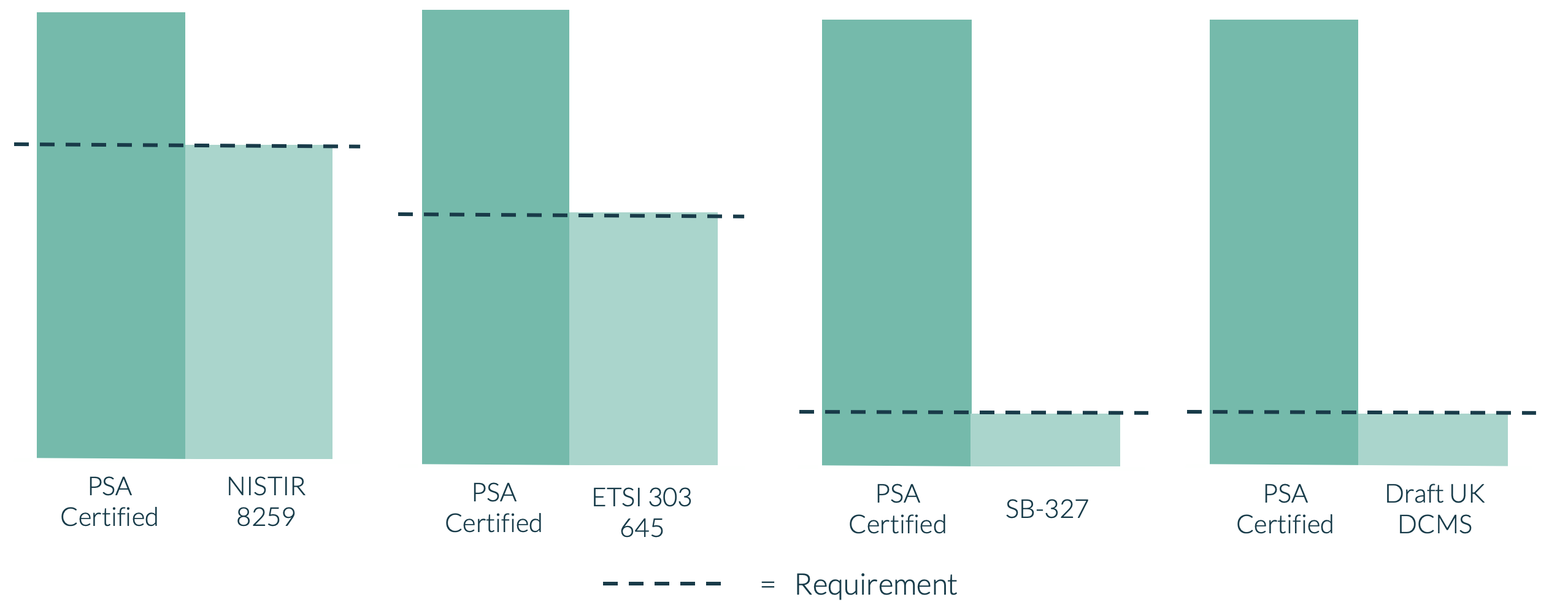
At the end of the new PSA Certified Level 1 questionnaire there is an appendix showing the mapping of PSA Certified questions to the requirements set in these other documents. This will guide device makers, who can turn to PSA Certified and know they have a security scheme that has been methodically developed from IoT threat models and has a test lab-based security assessment. PSA Certified has become the “go to” for documents, open source software and now IoT security assessment.
This is just one of the exciting updates were announcing this year. Why not check out our momentum blog which covers our reflection on key achievements in the last twelve months and exciting updates surrounding the PSA Certified program. In this blog we will touch on new government standards and regulatory alignment with PSA Certified Level 1, the wave of world-leading silicon providers achieving PSA Certified Level 2, plus critical momentum we’ve seen from device manufacturers embracing their role in security for digital transformation.
The Future
With the evolution of our growing modern digital economy and the pace of IoT deployment only accelerating into the future, it is vital to ensure every IoT device is protected. It is essential that these devices build in security at the design stage, starting with the Root of Trust to provide a trust anchor for the device, the data that flows from it and the services that need to trust the data.
PSA Certified has the momentum to heal the fragmented world of IoT security and offer a comprehensive solution that is leading to broad industry adoption. You can see the long list of PSA Certified products here.
