In this blog, we explore the value of a Root of Trust for device manufacturers, the challenges faced when implementing a Root of Trust, and how a standardized Root of Trust is providing a solution.
By 2025 it is expected that there will be approximately 55.7 billion connected devices, each of them bringing new levels of service and efficiency, fueling digital transformation across all industries. However, the increase of Internet of Things (IoT) devices also brings with it a rise in hacks, with all forms of cybercrime already costing an estimated £27 billion in the UK alone.
Security is therefore a rising priority for the industry: the PSA Certified 2023 Security Report found that 75% say security has increased as a business priority in the past 12 months. Security is no longer an option, but a necessity. Taking this into account, consumers and businesses are increasingly understanding the value of selecting devices built on trusted components. 58% of tech decision-makers said they consider building devices with trusted components or on the Root of Trust (RoT) as the most essential factor in creating secure devices and ensuring a secure future.

What Is a Root of Trust?
A RoT is a foundational security element of a connected device, providing a source of integrity, authenticity, and confidentiality for an entire system. While definitions of a RoT may vary, they are largely aligned on the notion that the RoT performs a set of implicitly trusted functions that the rest of the system or device can use to perform critical security functions, including providing a safe place for system-critical data and secrets. It can be a stand-alone security module or implemented as a security module within a chip. The RoT acts as an anchor on which manufacturers can build their chain of trust.
However, despite being a critical element of security design, many Original Equipment Manufacturers (OEMs) have been unable to take advantage of the benefits of a RoT. A lack of expertise, the fragmented RoT landscape, and a perceived lack of demand have made it seem too expensive, too time-consuming, and too complex for them to implement a RoT into every connected device.
In this blog, we explore both the technical and business benefits of a RoT to OEMs, why OEMs have struggled to implement them in the past, and how PSA Certified is providing a standardized RoT, in the form of the PSA-RoT, that is unlocking the value for OEMs.
How Does a RoT Make a Device More Secure?
Implemented into the chip and leveraged through the system software to the end device, the RoT is the part of a processor where all security operations are performed. Without a RoT, there’s an agreement in the ecosystem that a device cannot be trusted, and it leaves the door open for adversaries to cause harm, for example:

Compromising Unique Identification: Without a RoT, the identity of a device cannot be verified with absolute certainty. Any service that relies on that identity can never be sure that it is talking to the device it thinks it is. It could be communicating with a clone or a device that is sharing data with other unknown devices.

Compromising Secure Software Updates: Attempts to update the software version can be halted if the update itself is not protected by a RoT. An attacker may even be able to reverse a securely applied update if the RoT does not detect the hacker’s attempts to re-introduce old and vulnerable code.

Compromising Secure Boot: A RoT is essential to ensure that only authorized code is executed. If secure boot and secure loading processes are not enabled unauthorized malicious software may be allowed.

Compromising Trusted Services: Without a RoT, the sensitive processing that is needed to be able to trust a device is not isolated from the rest of the likely untrusted implementation. This makes it nearly impossible to check for security risks, giving an attacker many ways to extract the data and subvert the operation of a device.
When a RoT is properly implemented it enables security functionality, meaning that every device with a RoT has the potential to fulfill the promise of ‘security by design’, ensuring all devices can be trusted, encouraging mass adoption of the IoT, and unlocking the possibilities of a connected world.
What Are the Business Benefits of a RoT for OEMs?
There are also several business benefits of implementing a RoT. Our research shows that while consumers previously bought products based only on features, now they’re buying a product based on features and security. The PSA Certified 2022 Security Report found that an overwhelming 83% of respondents look for specific security credentials when buying IoT devices as a consumer. This gives OEMs who adopt a RoT-based solution the opportunity to break into new areas, positioning themselves as early adopters in emerging markets (such as the smart home and smart city industry), and leading the IoT into new markets, traditionally seen as too high risk, for example, critical services or the medical industry.
Similarly offering a RoT provides customers with a level of assurance that increases their confidence levels and helps promote IoT adoption. 69% of tech decision-makers agree that you can charge a premium for products with security built-in, as it increases trust and helps technology to scaler faster. Speaking on the #beyondthenow podcast, Jan Munther (Head of Digital Product Security at ams OSRAM) also highlights how security is increasingly becoming a unique selling point: “If you have a device that is factually more secure than the competition, it is in any case added value.”

In addition, governments and standards bodies are starting to mandate security requirements, which can only really be met through the use of a RoT. For example, one of the requirements in the ETSI EN 303 645 standard is ‘Securely store sensitive security parameters’. Storage is only secure if private data is bound to a device to prevent it from being cloned or disclosed outside of the device. Confidentiality is typically achieved using secure keys, which are reliant on cryptographic services enabled by the RoT.
Implementing a RoT also provides assurances for the wider ecosystem, such as for insurance providers. The complexity, insecurity, and dynamic nature of the IoT makes it hard for insurers to quantify risk and provide the protection that OEMs need. Peter Armstrong (former cyber-insurance expert, Munich Re) says that a standardized RoT can help combat these challenges, allowing insurers to model risk and minimize front end variables: “Without [a RoT], we won’t be able to identify the breakdown of liability in these value chains, and we won’t be able to offer the necessary insurance capital.”
The Value of a RoT for Different End-Market Verticals
| Asset Tracker | Smart Voice Assistant | Smart Streetlights |
|---|---|---|
| What is an asset tracker? Asset trackers are used to track assets, often in transit, to ensure they reach their desired location correctly. These devices can often be of interest to adversaries as they can use vulnerabilities to detect where an item is. | What is a smart voice assistant? Smart voice assistants and smart speakers are voice-activated devices that complete many tasks including playing music, answering questions, and integrating and controlling other smart home devices, such as smart lights. | What are smart streetlights? Smart streetlights are contributing to the emergence of smart cities providing a more efficient way to run this critical service. As well as turning on and off autonomously they can also provide information on when a light has stopped working. |
| The key security concerns/attack vectors? Due to a lack of physical access, normally hacks would take place remotely. One example of a hack on an asset tracker would be a man-in-the-middle attack where an adversary interrupts communication on a device in order to disclose or modify the location of the tracker. | The key security concerns/attack vectors? One example of a hack on a smart speaker would be an impersonation attack, where the hacker impersonates a legitimate admin user on the speaker to gain access to voice records, modify configuration, or impersonate the user. | The key security concerns/attack vectors? Due to its positioning in the public domain, a physical attack could likely take place on this device. An attacker may be able to load code that controls the lighting in a way that is dangerous to the citizens, or in a way that is used to aid in crime activities. |
| How does a Root of Trust mitigate this? The Root of Trust establishes secure communication between the device and the server/cloud to ensure that messages can be exchanged securely. | How does a Root of Trust mitigate this? The Root of Trust allows a unique identity to be assigned to a device and ensures that this identity is attestable. This identity facilitates trusted interaction with the device. | How does a Root of Trust mitigate this? The Root of Trust ensures that only legitimate code can be executed, preventing an attacker from loading their malicious code. |
Challenges Limiting the Adoption of a RoT by Device Manufacturers
Despite the benefits of a RoT, adoption by OEMs has been limited for several reasons. Firstly, there was a lack of readily available chips that had a RoT implemented in them, lengthening the procurement process and time-to-market. Similarly, where chips were available there were substantial differences in the RoT implementation, with each silicon vendor creating their RoT in a different way with different APIs (Application Programming Interfaces) to access the security functions within it.
Consequently, OEMs were faced with chips with different security functions and different APIs, making it too complex, too costly, and too time-consuming to utilize the RoT in their devices. Similarly, the fragmentation of architectures, meant that OEMs did not have the time to develop the necessary skills to manage RoT implementation in an adequate, scalable manner for mass adoption.
So, how can OEMs overcome these technical challenges and unlock the benefits of a RoT?
A standardized RoT across the chip ecosystem is key.
How a Standardized RoT Can Help OEMs
Standardization of the RoT plays to the strength of the value chain by allowing the different parties to focus on what they are good at. The RoT suppliers can focus on implementing the core security functionality required in IoT products, while OEMs can spend their time developing IoT innovations, without having to focus on implementing the security capabilities that the RoT delivers.
In addition to this, the use of a common RoT across different products and applications means that the security functionality provided by this one component can be used in multiple devices. A standardized RoT is a highly scalable method of delivering security capabilities on a large scale.
A standardized RoT, therefore decreased the security burden for OEMs, reducing the need for, and cost of specific expertise, without increasing time-to-market. A standardized RoT also builds trust with insurers, enabling them to offer warranties on devices and facilitating greater innovation in the IoT. Similarly, having the RoT independently evaluated and certified validates security implementations, showcases alignment to standards and regulations, and provides assurances for end-customers.
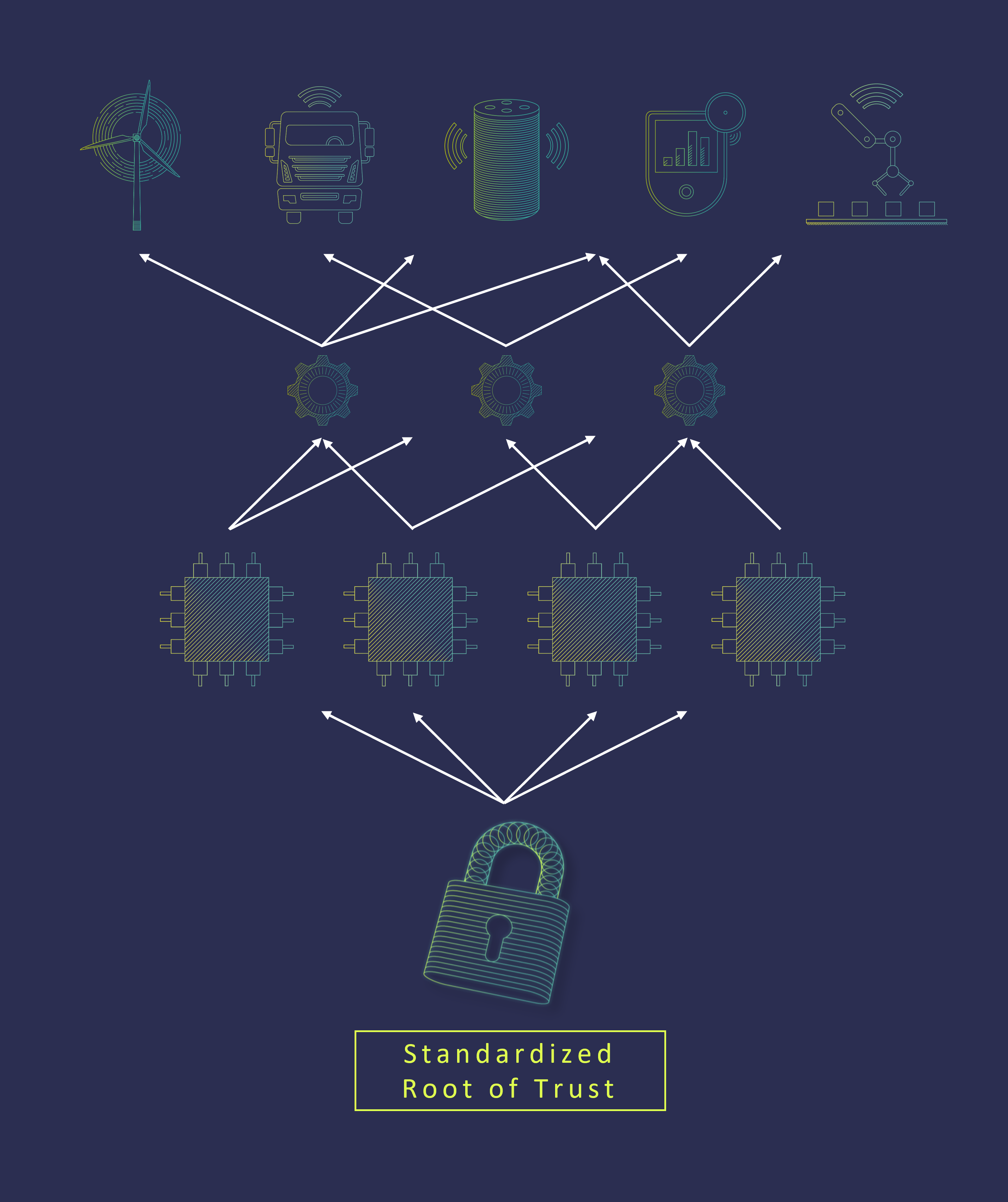
The PSA Root of Trust: Unlocking Value for Device Manufacturers
PSA Certified is an IoT security framework and certification scheme, developed by security experts with a mission to democratize IoT security. As part of this, the founders of the scheme recognized the need for a standardized RoT built in collaboration with the world’s top chip vendors. The PSA Root of Trust (PSA-RoT) provides that standardization, ensuring that device manufacturers can use the PSA-RoT from different chip vendors, understand the security functions that it provides, and the level of security robustness that it offers. PSA Certified also provides a common set of APIs, in the form of the PSA Functional APIs, that makes it quicker and easier for OEMs to interface to the chip’s PSA-RoT.
PSA Certified provides free agnostic technical guidance documents to help guide the design and integration of the PSA-RoT, including the Platform Security Model, the Platform Security Boot Guide, and the Cryptography API Specifications. PSA Certified co-founder, Arm, has also published guides to help design PSA Certified compliant systems based on arm processors, including the Platform Security Guide for A-Profile and Trusted Base System Architecture for M-Profile.
