In the early days of the Internet of Things (IoT), security was not always at the top of people’s minds. Protecting a connected device was difficult, and it took up valuable time and resources. As a result, companies did not fully understand the risks or could not incur extra costs or face delays when they were racing to get their products to market.
Since then, some things have changed. Now, we understand the importance of security and the need for all operations to take place on components that have a critical baseline of security built in. However, the challenges associated with implementation remain. What software or hardware platform do you build your product on? How do you balance the competing demands of profitability, interoperability and security, while developing value-adding features and reducing your time to market?
In addition, security is still complex. It involves a combination of hardware and software security features and validating them before they are utilized is a lengthy process that is best carried out by experts. Unfortunately, time and security expertise are often in short supply.
That means the electronics industry has to address a significant challenge. The potential of the IoT will be limited if our devices are not secure because customers will not be able to trust devices or the data that is being generated by them. If we want to build customers’ confidence in our technologies, we have to ensure security is more accessible, and quicker and easier for everyone.
Building on the Ecosystem’s Expertise
We can start by taking a layered approach to security. To explain in more detail, if you are trying to protect the data that is being gathered and disseminated by a device, you can add encryption at the application layer. However, what happens if an attacker bypasses that encryption? If there are weaknesses in the operating system (OS), storage, network or hardware layer security, the hacker will have easy access to your customer’s data.
To protect it and the device, security and trust should be established within every layer and for that you need to look to the ecosystem for support. By using an IoT platform that draws on best practice from across the industry you can ensure that a wide range of vulnerabilities have been considered and that you are building on firm foundations.

Capitalizing on the Security Features in the Silicon
Security cannot be an afterthought. It should be integral to the device. So, to design-in security from the ground up, OS providers should take advantage of the security capabilities that are built into the hardware. The security functions in the Root of Trust (RoT) can be leveraged to create a space where all trusted operations can happen securely.
Then, we need to create a consistent and easy-to-use interface to the security functions that exist within the secure processing environment. APIs give developers access and make the task of securing the software more straightforward.
“IoT security is still in its infancy and the rules of the game are changing,” explains Murat Cakmak, Founder and CEO of the UK-based operating system developer, ZAYA. “IoT device manufacturers are finally waking up to the need to protect data and ensure privacy, so we added security as a design element that not only ensures the OS is secure, but helps secure the product, too.”
Making Complex Security Functions More Accessible
How does this change the way you work? To make complex security functions more accessible, we have developed the PSA Certified framework and assurance scheme. It makes it quicker and easier to secure your software because it provides clear guidance, free security resources and a matching certification program.
“Although there are several security certification processes available, PSA Certified is the only one that goes right to the heart of the device, to the operating system and the silicon itself,” says Christophe Mani, STM32 ecosystem security marketing manager at ST. “It validates that the hardware implementation and OS have robust security in place and that the platform is secure.”
It has also been developed by industry leading security experts, as Kevin Townsend, Senior Embedded Engineer with Linaro, an open source collaborative engineering organization and member of the Zephyr Project, explains: “Features like cryptography are hard to implement simply because there are so many options for different algorithms and different libraries. It’s important to choose cryptographic algorithms that are up to date with vulnerabilities that are out there today, and not everybody has this knowledge. With Zephyr and Trusted Firmware-M (TF-M), those specific technical decisions have already been dealt with by experts.”

The scheme includes several core building blocks:
Standardized and Verified Components
PSA Certified enables you to utilize components that are independently assessed as having security built in, which will help you reduce your reliance on security experts, minimize risk, and reduce time to market. The world’s leading silicon and RTOS vendors have developed standardized and certified components for you to build on. As Christophe Mani, STM32 ecosystem security marketing manager at ST says: “We have to take a mass-market approach to security with shared information and standards so that all of our customers, right down to the sole proprietor in his or her garage, can make a device that is secure and meets local regulations at a price point the market can tolerate.”
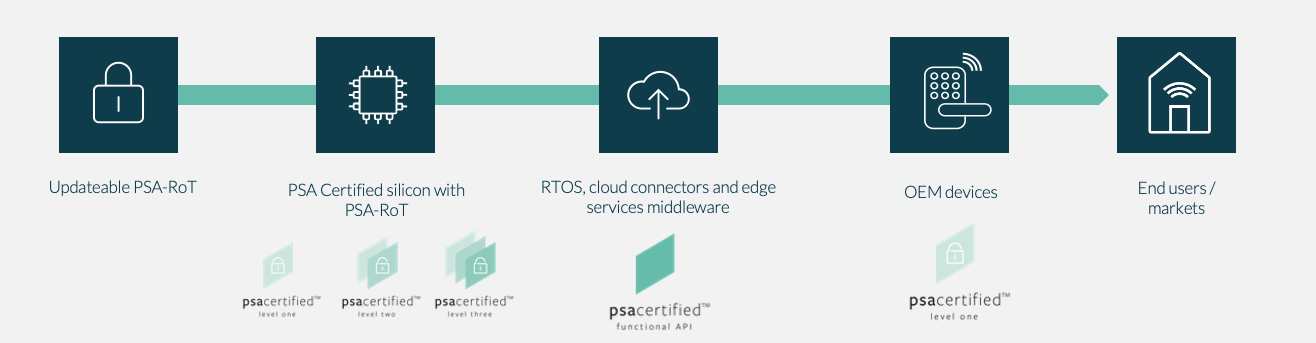
The PSA Root of Trust (PSA-RoT)
The PSA-RoT is an easy-to-use on-chip component that has been designed for the IoT. It is made up of isolated, trusted hardware and trusted firmware that provides essential security functions – typically cryptography, attestation, trusted boot and secure storage – in a secure processing environment. Security is built into the PSA-RoT by silicon vendors. PSA Certified then evaluates the implementation of the PSA-RoT component in the chips.
PSA Functional APIs
However, it is one thing to have proven security and another to be able to maximize the benefits of it. PSA FunctionalAPIs hide the complexity of the PSA-RoT and give developers access to the trusted functions. That means they can get security right the first time without creating their own solutions, which saves significant time and cost, and it means they can focus their attention on creating stand-out features instead. The PSA Functional APIs are supported by silicon vendors and system software providers. Certified products support these APIs and enable device manufacturers to call the APIs for any trusted functions.
Kevin Townsend describes the impact this approach to security has on his customers: “PSA Certified means that companies using Zephyr can start developing products with a high level of assurance that the product is going to meet minimum security standards right out of the box. PSA gives the IoT community specialized, up-to-date knowledge and out-of-the box functionality upon which to build their own systems.”
Trusted Resources
So, where do you start?
Step 1: Learn more about building trust in your devices, and the wider IoT, and the PSA Certified framework.
Step 2: Explore the range of off-the-shelf security system software that has been provided by members of the ecosystem. For example:
Trusted Firmware-M is the reference implementation of the PSA Root of Trust, implementing security functions and supporting the PSA Functional APIs in the chip.
APIs are freely available through the PSA Certified ecosystem.
Also, look for the PSA Certified logo, which will help you find hardware and software components that are easy to use and built upon security.
Step 3: Check your approach to security is in line with industry best practice, as well as current and emerging security regulations, requirements and laws, then provide evidence of that to your customers.
Quote
Just 2-years ago, ZAYA was secure but when manufacturers asked for proof, we didn’t have any. Now we can just show them the PSA Certified accreditation, which proves we’ve been assessed by an independent authority.
Overall, making security easier to implement, even for people who are not experts in that field, will help companies:
Balance their priorities: so that there is no trade-off between security, quality and profitability.
Save time: re-usable code improves time-to-market and developers will spend less time patching holes in security later if it is built-in.
Reduce costs: drawing on lessons learned from across the industry lowers research and development costs, as well as the cost of security.
Minimize the risks to a company’s reputation and bottom line: a data breach has financial implications and can cause investors, shareholders and the public to lose trust.
Differentiate themselves: developers can spend more time on the value adding features that make a business stand out from its competitors’. The PSA Certified logo also gives companies a way to show their customers that they take security seriously.
Quote
PSA Certified saves us a lot of time and money because it means everyone involved the design, assembly, and implementation of our solution can work from the same security framework. Only the PSA Certified program provides detailed guidelines for the system architecture, not just the application layer. PSA is very organized across all layers and helps us avoid inefficient and lengthy development
Quote
Device manufacturers know that our platform is certified on the best global standards which means they can follow those standards, too, and we don’t need to open up our product source code for verification or provide stacks of documentation.
Quote
With the IoT expanding to include devices in more categories, such as healthcare and household products, companies must be able to create IoT devices that consumers trust. PSA Certified shows that the ST solution is secure and easy to implement. Device manufacturers can offer consumer products that are less impacted by price and can innovate quickly without the heavy burden of specialized engineering expertise.
