As the number of edge devices continues to rise, the need for security assurance is increasing. However, securing Linux devices remains a complex and time-consuming task. This blog explores these complexities and how the PSA Certified ecosystem is simplifying the security journey for Linux-based device manufacturers.
Much of the growth in the IoT space is being driven by devices with ever-increasing processing capabilities, driving a growing requirement for security at the edge. These powerful solutions can make our lives easier and are evolving to become increasingly more integrated into our daily routines. Unfortunately, this means that thanks to our ever-more-connected world, compromising these devices can disrupt consumers’ lives and create a significant loss of confidence in connected devices.

Why is Securing Linux Devices So Complex?
Implementing solutions that are based on robust security can be complex and time-consuming, and unfortunately, cost and time-to-market pressures have resulted in many products being deployed with unintended security vulnerabilities. Too often developers of devices based on Linux assume that necessary security features are taken care of, but this is not the case for most off-the-shelf distros. In the real world, this has resulted in compromises that range from issues such as the public access of security camera images to more catastrophic attacks, like the botnet attack where malware was installed onto Linux-based devices, that hackers then used to execute denial of service attacks on the internet.
Why is developing and deploying security on the Linux system so complex? Well, the answer to that is also complex. For a Linux system to have robustness, it requires some form of Trusted Execution Environment (TEE), operating behind a hardware-enforced process separation. This provides security services and assures that if Linux is compromised, security-critical portions of the system remain safe. There are also additional security requirements such as secure provisioning of devices on the production line, seamless deployment of these devices into the field, and secure software updates of devices in the field – these requirements are challenging, yet vital for secure device management over a product’s lifecycle.
This secure underpinning of a device’s operating system is what we refer to as a silicon Root of Trust (RoT). This part is silicon specific and includes the hardware needed to enforce isolation of the Secure and Non-secure Processing Environments, and the secure execution environment running in this isolated environment. This RoT is important to developers because it abstracts the critical security functions away from their application development while still providing the required features.
Security Requirements for Linux Devices
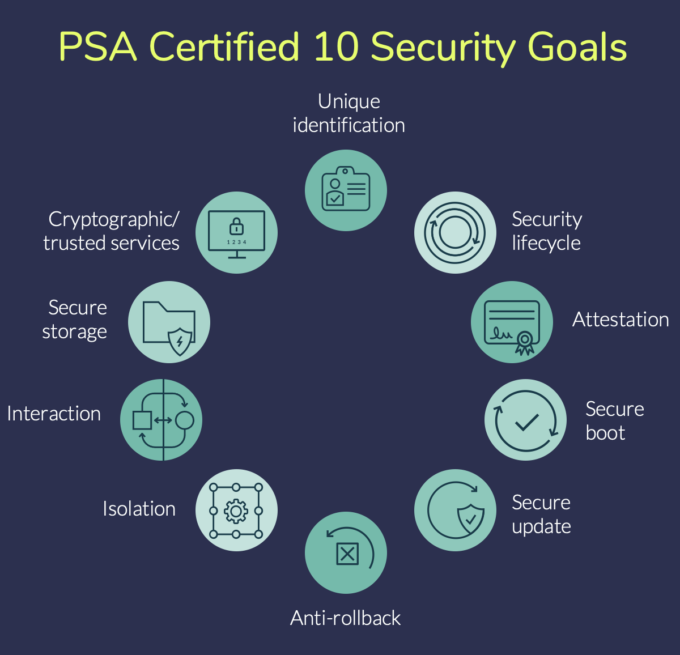
Of course, this poses the question: what are the required features? At PSA Certified we conducted threat model-based assessments of common IoT products and developed the PSA Certified 10 Security Goals. These goals, alongside government requirements and ongoing research, formed the basis of the requirements for a software system to become PSA Certified. For endpoint device developers, the advantage of using PSA Certified components like chips and system software is that they can develop their products knowing that they are using components that have passed the scrutiny of the independent, lab-based evaluations need to obtain PSA Certified.
Made Possible by the PSA-RoT Ecosystem
The good news is that achieving best practice security for Linux doesn’t need to be a solo effort. In fact, there are several PSA Certified partners who can help add robustness to your products. Let’s look at a case study in this space from PSA Certified Level 1 partner, Foundries.io.
Case study: Foundries.io
Foundries.io, has developed a cloud-based secure micro platform, built on Linux, that is designed to enable customers to get to market quicker with secure IoT and Edge devices. FoundriesFactory enables customers to utilize and customize this Linux micro platform for their specific hardware end-user case needs. It also considered requirements across the lifespan of a product from development, test, deployment, and maintenance.
The development cycle enables customization of firmware, kernel, OS, and user space to match their specific hardware and end-use case needs. All of this can be managed within a private source code area where they can incorporate any proprietary IP. The customer’s IP, services, and apps can then be added into the build system which enables release tagging and securing the devices with device-to-cloud security.
As recognized in the PSA Certified 10 Security Goals, for a device to truly be “secure”, product deployment and maintenance are also vital to enable a device to remain secure throughout its installed life. A secure over-the-air (OTA) update approach is vital to protect a device long-term and it’s important to recognize that not all update approaches are secure. FoundriesFactory is compliant with The Update Framework (TUF), adding additional robustness with end-to-end signing and verification of image artifacts for authenticity and integrity. FoundriesFactory was recently awarded PSA Certified Level 1 and also implements the PSA-RoT as specified by PSA Certified when paired with a SoC which also implements the PSA-RoT.

The Journey for a Linux-Based OEM using Foundries Factory
So, let’s look at a hypothetical use case for an OEM who is developing a secure, network-connected camera system and how they could reach PSA Certified Level 1. The OEM developer can select a PSA Certified chip that is running OP-TEE and provides an evaluated PSA-RoT. From here, you can select a software platform, such as FoundriesFactory, that can be used to configure a version of their PSA Certified Linux MicroPlatform for their selected chip.
From here it is a straightforward task for the developer to implement the camera system. Once the design is complete the developer can then leverage the selection of PSA Certified chip and system software components to take the product through its own PSA Certified Level 1 evaluation. Selecting pre-certified silicon and system software simplifies the certification journey for OEMs who then only need to complete the top-level security questions in the PSA Certified Level 1 questionnaire- which is less than 20 questions.
With all this in mind, your consumers can trust your device knowing that the security-critical components of the system have passed independent lab-based security evaluations, and rest easy knowing that you’ll secure OTA updates throughout the lifecycle of the camera.
Don’t Ignore Security at the Edge
Security at the edge is too important to be ignored. Failing to build-in product security solutions will erode consumer confidence, create barriers to market growth and spawn onerous regulations that will stifle innovation. In the current market, there is no longer an excuse for failing to implement best practice security into your product. To minimize risk and shorten time-to-market, the use of PSA Certified components can give developers peace of mind that they have selected products that have been certified to the standardized requirements of PSA Certified. An additional benefit of using PSA Certified components is the ability to take the final product through its own PSA Certified evaluation, thus assuring that the products align to NISTIR 8259A, Californian State Law SB-327, and ETSI EN 303 security standards.
Next Steps
PSA Certified is a global partnership aimed at simplifying IoT security and unifying the industry under a common language. Learn how you can join the PSA Certified ecosystem.
