The Internet of Things (IoT) is already reshaping industries, but some of these connected technologies will help us take the next step forward. Edge devices are more complex and powerful than other IoT products, which creates a world of possibility. However, they are still vulnerable to cyberattacks and need to have right-size security designed in from the beginning of product development.
IoT devices that can process, analyze, and store data themselves, rather than sending it all to a centralized cloud-based location such as a data center, are known as edge devices. They include well-known products such as smart speakers, connected thermostats, smart meters, security cameras, robotics, routers, and intelligent gateways. Edge devices are deployed in a range of settings, from manufacturing to healthcare, transportation, and agriculture. They are underpinning smart cities, making autonomous mobility possible, and giving us more control over our home environment.
Why Are Edge Devices Important?
Processing information on a device, or at the edge of the network using gateways, will help us manage the extraordinary amount of information that is being generated by IoT products. According to analysts, IoT data is already the fastest-growing data segment. So, as we continue to move towards a world of one trillion connected devices, there are fears that adding more to it will overwhelm the current infrastructure. Edge devices solve this problem by processing the data locally and only sending the relevant critical data back to the cloud.
As well as helping us manage data more effectively, edge devices also help improve efficiency and performance. As Santhosh Rao, Senior Research Director at advisory firm Gartner, explained in an article: “As the volume and velocity of data increases, so too does the inefficiency of streaming all this information to a cloud or data center for processing.” Processing data at the edge reduces bandwidth requirements and enables data to be analyzed in real-time. Similarly, processing data at the edge helps organizations mitigate the impact of outages because they are not reliant on being connected to an external network. This is vital for the delivery of essential services.
Gartner predicts that by 2025, three-quarters of enterprise-generated data will be created and processed “outside a traditional centralized data center or cloud”. That is up from 10% three years ago. However, for some, the benefits of the edge do not yet outweigh the potential costs. The lack of security in edge devices is stopping some organizations from investing in such technologies.

The Security of Edge Devices
As with any connected device hackers will always be keen to find and exploit weaknesses, however, due to the amount of sensitive data collected by edge devices the incentive for hackers is much greater than with more traditional simpler IoT devices. The rise in the number of edge devices and the move towards edge computing within companies, is increasing the attack surface for hackers, enabling both physical and remote hacks, as well as giving them access to greater amounts of data.
Devices that rely on cloud computing have the advantage of additional security: servers in data centers are protected by doors, locks, security cameras, and firewalls. Edge devices are usually deployed remotely: they could be in a factory, beside a railway line, or even in a field- all locations where people have easy physical access to them. Additionally, many edge devices help operators run critical infrastructure, for example, water treatment plants or transportation systems. The easy access to edge devices and the high value of the assets increases motivation for hackers.
To ease concerns about security and build the necessary trust in edge devices and the data they generate, we must ensure that best practice security is designed-in to every connected device and is maintained over the lifetime of a device- which could be 10 years or more. This is because a weakness in a single device can have a serious impact on the wider system, operating environment, or on people’s lives.
The Challenges of Securing an Edge Device
While all IoT devices are vulnerable to cyberattacks, the manufacturers of edge devices must overcome some unique security challenges. Firstly,edge devices have complex hardware, software, and connectivity requirements. They are just as intricate as a server, and yet, as we mentioned previously, they are not locked away behind physical barriers or firewalls or protected from external networks. That makes them vulnerable to a multitude of potential hacks. Establishing the threats in scope might sound simple, but it’s a complex process that requires security expertise to carry out effectively.

Unified end-to-end orchestration is a priority for enterprises looking to use edge devices, and this requires merging the worlds of information technology (IT) and operational technology (OT).This is challenging and requires significant innovation in software and services. The software must be built on fundamental Root of Trust (RoT) services for identity, remote attestation, and provisioning secrets. It is also vital that security spans the entire data journey, from devices and infrastructure to software and data. This requires expertise and an understanding of different types of software and hardware. For example, for an edge device based on Linux to be secured, the system requires some form of Trusted Execution Environment (TEE), operating behind a hardware-enforced process separation. This provides security services and assures that if Linux is compromised, security-critical portions of the system remain safe. These requirements are challenging but also necessary to securely manage an edge device over its lifecycle.
Overcoming Edge Security Challenges
A standardized approach to the security built on a common set of requirements is crucial if we are overcome these challenges and democratize security. At the heart of this is the implementation of a common hardware-based RoT as the secure foundation of every connected device. Built into the silicon, a RoT completes a set of implicitly trusted functions that the rest of the system can use to ensure security and provides a source of confidentiality and integrity for the whole value chain. Standardized approaches enable silicon vendors to implement a RoT quickly and cost-effectively, while the security burden is reduced for software providers and OEMs as they can rely on a secure foundation.
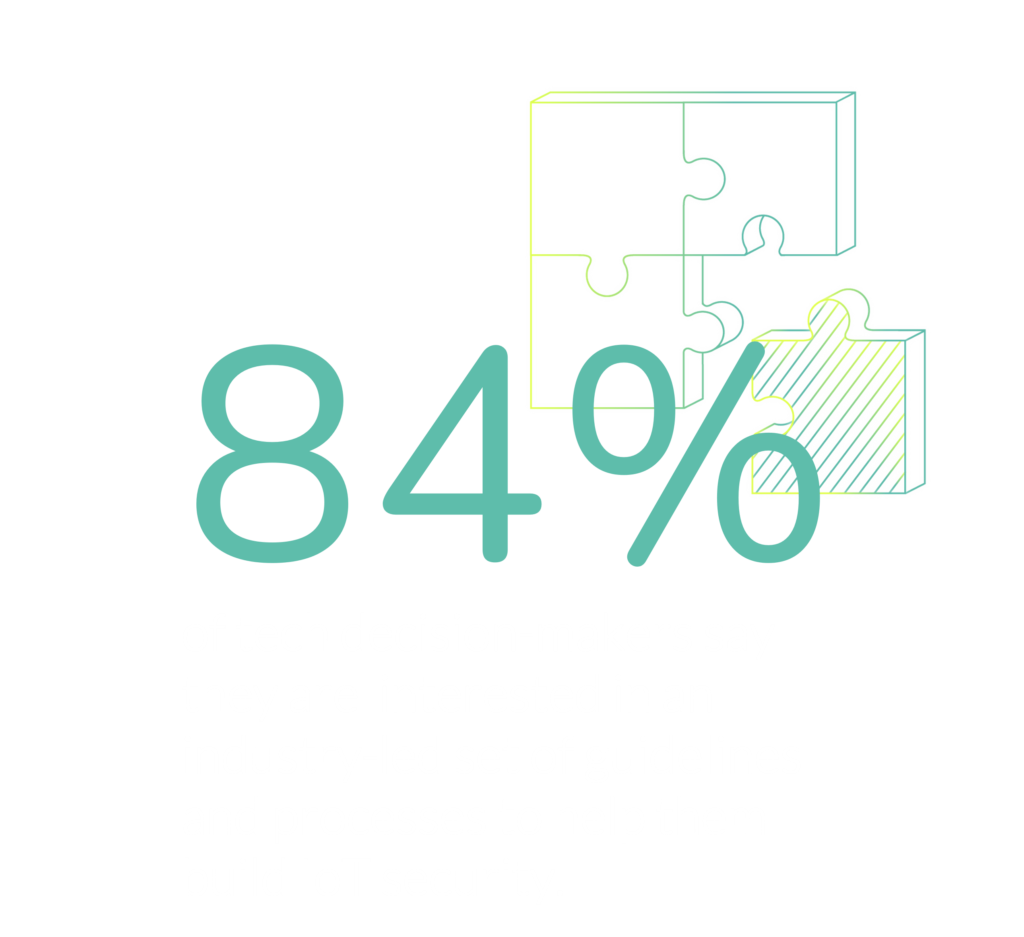
The alignment of fundamental security principles for every device is also key to ensure that basic security measures are not being missed or skipped. While each device will have unique security requirements, there are a set of common requirements that should be implemented into every connected device. Functions such as attestation and cryptography are particularly important for edge devices, but only work effectively when employed with other best practice security functions. Security needs to be approached holistically, with both hardware and software security considered and built into the DNA of every IoT device. With 84% of technology decision-makers interested in an industry-led set of guidelines and processes to help build IoT security, the whole ecosystem must collaborate to establish a common baseline and unlock the potential of the edge.
A Partnership Providing the Confidence to Create
PSA Certified provides a security framework and independent evaluation scheme, with a mission to ensure every connected device is built on a Root of Trust, providing a foundation for scalable, trusted deployments. 10 Security Goals are outlined and assessed to ensure common security requirements are implemented into every connected device. This layered approach to certifications enables the ecosystem to collaborate and leverage the security expertise and efforts across the value chain. PSA Certified provides the confidence to create new products and implement new services by providing assurance across the ecosystem.
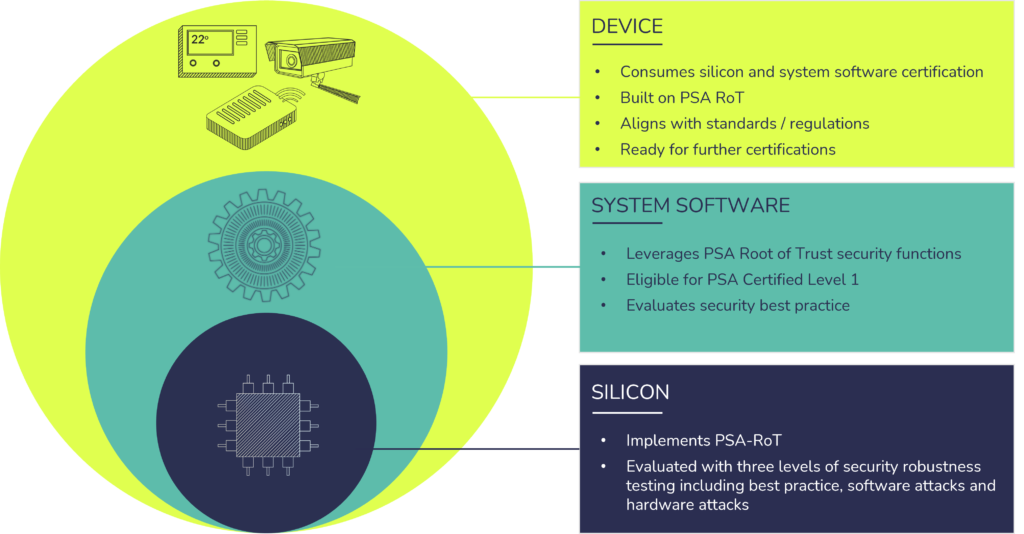
The Role of the Ecosystem in Securing Edge Devices
We are already seeing the development of different solutions from across the industry looking to reduce the security burden for edge devices. PSA Certified partner Foundries.io have developed a cloud-based secure micro platform, built on Linux, that is designed to enable customers to get to market quicker with secure edge devices. Recognizing the importance of a secure lifecycle for edge devices, the secure FoundriesFactory software platform utilizes a secure over-the-air (OTA) update approach to help OEMs meet this requirement.
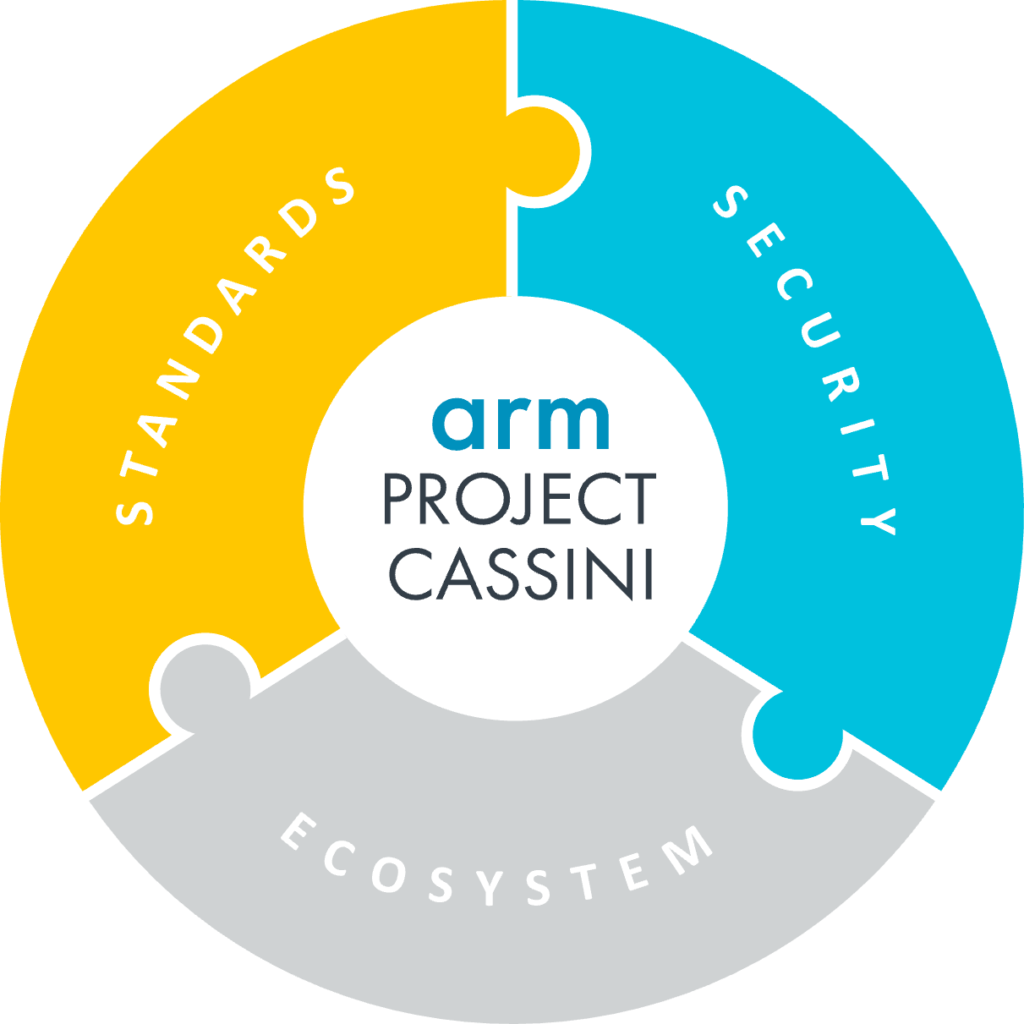
PSA Certified founder and world-leading semiconductor IP company Arm is paving the way for more secure edge devices with Project Cassini. PSA Certified was chosen as one of the three pillars of Project Cassini, as it plays a central role in uniting the ecosystem under a common security language, reducing fragmentation, and democratizing security access. After two years of engineering effort and extensive Arm ecosystem collaboration, Project Cassini is now backed by over 70 partners, including a number of PSA Certified certifications from Gigabyte, Foundries, NXP, Eurotech, and Rockchip. It’s great to have PSA Certified recognized in Project Cassini, as part of their promise to deliver a seamless cloud-native software experience across a secure edge ecosystem with certified hardware, software support, and ecosystem engagement.
Secure Your Edge Device by Calling on Experts from Across the Globe

Next Steps
Discover how PSA Certified can help you secure your edge devices in this program overview.
