The following article is written by our partners at Infineon Technologies as part of our In conversation with … series.
We live in a hyper-connected world. Once ordinary products, from security cameras to energy meters, medical devices and cars, are now part of the Internet of Things (IoT) and are generating vast amounts of data. When that information is processed – locally, at the edge or in the cloud – it can transform businesses and industries. In the automotive sector, for example, driver assistance technologies are rapidly advancing, and we will soon have fully autonomous vehicles. In smart factories, sensors and robots are helping to improve productivity. While in cities, data is constantly being transmitted through data centers over high-speed networks.
The question is how secure is that data? And what can we do to protect it from cyberattacks, especially when devices rely on it being available around the clock?
Securing Connected Systems
Critical data, such as boot code, security keys, certificates, biometric sensor data and passwords, keep connected systems running and are stored on Flash memory devices. However, the importance of that information makes the technology an attractive target for hackers. For example, Flash devices may be vulnerable to:
- An impersonation attack, where a hacker poses as known or trusted person to carry out a secure transaction.
- An attacker who tries to clone the Flash device and its contents.
- Replay attacks that are intended to delay or repeat data transmission.
- Someone who may attempt to steal secret keys.
- Theft of information, which can occur through snooping attacks.
- Or someone who is trying to reverse-engineer a device’s cryptography system by collecting information on cryptographic computation through side channel attacks.

If one of these attacks is successful, it would certainly be disruptive and could even be life threatening. That is because our customers are automotive original equipment manufacturers (OEMs) and Tier-1 suppliers working on ground-breaking initiatives such as advanced driver assistance systems and autonomous cars; smart meters and medical devices; and data center servers and 5G wireless infrastructure solutions. They must be able to trust their connected systems, protect their users’ data and their own intellectual property.
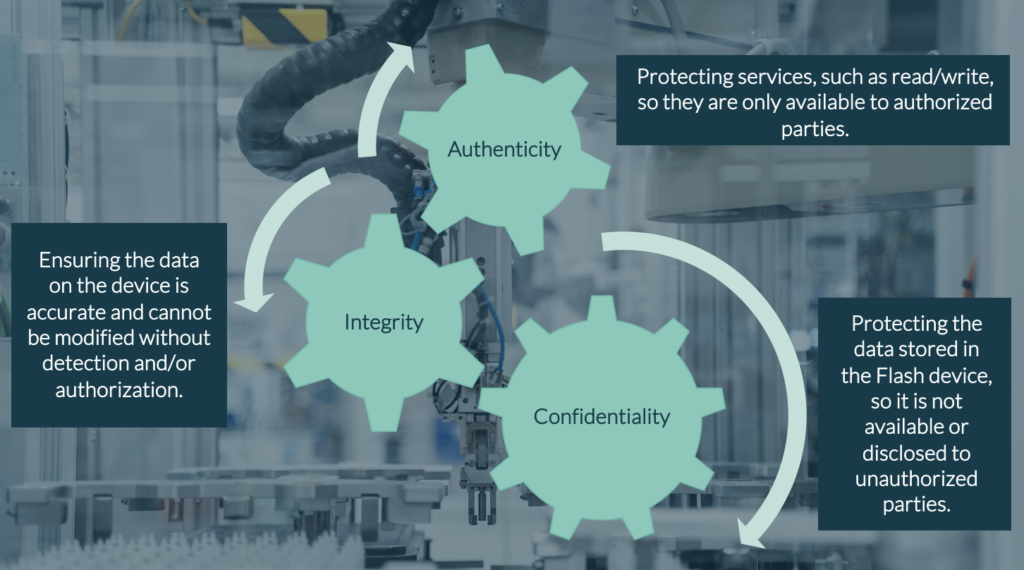
That places additional responsibility on the developers of the Flash devices that store valuable data. It means we have to build low-cost and scalable solutions around three key security principles:
Confidentiality: Protecting the data stored in the Flash device, so it is not available or disclosed to unauthorized parties.
Integrity: Ensuring the data on the device is accurate and cannot be modified without detection and/or authorization.
Authenticity: Protecting services, such as read/write, so they are only available to authorized parties.
Start with a Hardware Root of Trust
When Flash is external to the microcontroller unit (MCU), it is particularly vulnerable, which makes it critical that devices are designed with a secure boot process to ensure any content stored or retrieved can be trusted. When we were developing the SemperTM Secure NOR Flash device, we decided to build-in robust security by adding a hardware Root of Trust (RoT) with immutable and unclonable identity.
The hardware RoT provides hardware-protected secure storage for keys and certificates, preventing the modification or manipulation of stored data. It also enables end-to-end protection with authenticated and encrypted transactions; secure memory regions with configurable access controls; symmetric and asymmetric cryptographic algorithm support; and defense against side channel attacks.
In addition, flexible architecture with Arm Cortex®-M0 on-chip computing capabilities enables us to adapt and stay ahead of the constantly evolving security requirements.

Build on Best Practice
More and more customers are asking IoT product developers to provide evidence of their commitment to security, rather than just taking their word for it. In our case, we have complied with demanding functional safety standards for automotive and industrial applications to build our customers’ confidence in our solution. We can now assure customers that our products will operate reliably with minimal support.
We also wanted to certify our products using a trusted and industry-proven framework and assurance scheme. We chose PSA Certified for Semper Secure because it is an independent, multi-level IoT program that has been developed by security experts.
Being PSA Certified at Level 1 shows our customers we are serious about security and allows them to focus on their designs while we work hard to help them build trust in their devices. It also means our customers are confident in their IoT products’ security and can get to market faster.
How Secure Devices Benefit Customers
We need more efficient and effective security solutions to enable the transformation outlined earlier. That is, to help the automotive sector shift from driver assistance technologies to fully autonomous vehicles; to move the industrial market from in-service to predictive maintenance; and to enable the communications industry, including connected controls, to offer high bandwidth edge and cloud-based services for improved AI. With all of these developments, the need for secure, reliable, high-performing and high-density NOR Flash devices will increase and will enable:
Secure storage – Flash devices can be used to cryptographically store the sensitive system data organizations rely on and can also support authenticated and encrypted transactions.
Fast, secure boot – an increasing amount of software content along with stricter authentication and validation mechanisms can slow down the boot process of automotive systems. Fast secure boot begins with the read-only memory (ROM) in the secure processor and extends the trust to the external secured flash by a mutual authentication process that can get the system up and running within 100ms.
Secure over-the-air updates – a secure Flash device enables end-to-end security protection by allowing only authorized updates that can be managed directly from a remote server or cloud. This is useful in automotive applications because most cars have more than 100 electronic control units (ECUs) and more than 100 million lines of software code. It also enables remote device health monitoring by detecting any critical assets that are compromised and by restoring system integrity through a recovery mechanism.
As an industry, the increasing number of connected devices and the volume of data they generate means security is no longer just a bonus for customers. Security is now a necessity.
