The following article was written by our partners at Eurotech.
In recent years, data has become a sought-after commodity. Some people have used analogies to describe its importance in the modern world. British entrepreneur Clive Humby OBE coined the phrase ‘data is the new oil’ almost two decades ago. If he was right, we can think of edge devices as giving us a way to extract the oil and derive value from it.
Edge devices are connected leveraging Internet of Things (IoT) technologies, that enable organizations to collect, analyze, and store data from a wide range of internal and external sources on the device instead of sending the information to a cloud or data center.
They can be found in many settings from the transportation, energy and industrial sectors to telecommunications, healthcare, and home environments. The products include gateways, servers, routers and sensors and the more familiar security cameras or smart meters.
It is becoming increasingly important for IoT devices to have sufficient data crunching capabilities. In this blog, I explain why.
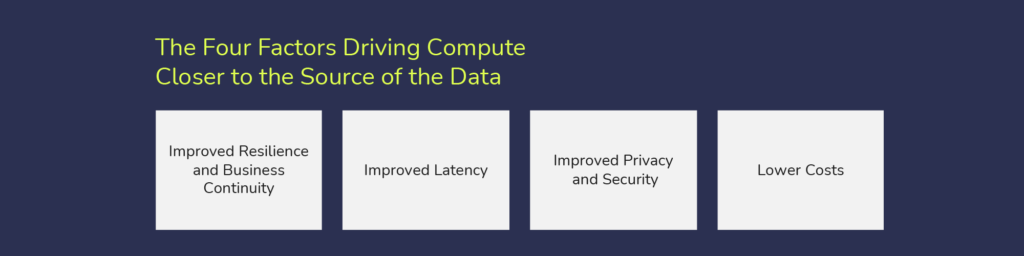
The Four Factors Driving Compute Closer to the Source of the Data
With a rapidly-increasing amount of data being generated every day, it’s clear we must find a more sustainable way to manage this incredible amount of information. There are four key reasons to make a shift:
Resilience and business continuity: organizations must be able to maintain their active operational status even if they are affected by unforeseen events. For example, a more distributed deployment scenario will enable firms to carry on despite downtime at a data center, connectivity problems or if some of the endpoint servers are no longer available.
Latency: depending on the application, organizations may not afford the time to transfer data to the cloud and back. If we consider industrial operations, in a predictive maintenance scenario for example, engine vibrations may be monitored up to every hundred milliseconds. It is not feasible for this amount of data to be sent to the cloud, analyzed, and returned in a timely manner.
Privacy and security: some of the data that is being generated may have to be gathered, analyzed, and stored in compliance with certain data governance principles, regulations, or laws. That may mean data must be managed at the edge – within a specific site, plant or in a specific geography. Organizations may not be able to keep data in the cloud and remain compliant.
Cost: transferring data is expensive so processing it at the edge may be more cost efficient.
More and more enterprises understand the potential benefits of collecting, analyzing, and storing information at the edge. Edge devices bring the agility of information technology (IT) to the operational technology (OT) environment to increase efficiency and enable new services. However, they also expose assets that have, until now, been isolated to a wide range of physical and digital threats.
The Importance of Securing Edge Devices
If we consider the IT environment, access to a data center may be restricted to prevent physical attacks on servers. Information and IT security may be managed to help keep a company’s or customers’ private data safe.
Edge devices, on the other hand, are likely to be deployed in a wide range of settings, from an organization’s headquarters to its factories or on its remote or mobile assets. That gives adversaries the opportunity to tamper with the technology and may leverage edge devices as new attack vectors to reach remote infrastructures. The amount of data being gathered also makes the edge devices attractive and valuable targets for hackers.
This makes securing the IoT infrastructure and its devices a top concern of many organizations.
More Organizations are Concerned about Security
Evidence suggests people are continuing to prioritize security. The PSA Certified 2023 Security Report, presents the results of our survey of more than 1,200 technology decision makers, found that 75% say security has increased as a business priority in the past 12 months. However, it also found 25% felt “very satisfied” with the level of security expertise within their firm.
With both interest in, and concerns about, security rising how can we ensure we are taking the right steps in our own security journey? And how do we assure our customers that the building blocks (in our case, the hardware, software and integrated hardware and software) we put in place are secure?
Eurotech and Deutsche Bahn
Eurotech worked with Deutsche Bahn in Germany to add connectivity to its locomotives. All its cargo trains have a Eurotech edge controller that interfaces with the field bus of the train itself, collecting 5,000 plus data points, to enable local alarming and local alerting in the locomotive. It collects and aggregates data and sends the summary of that data to the cloud. Data scientists can then exploit it to identify efficiencies in the operation and maintenance of the fleet.
Overcoming the Barriers to Security
The challenge we all face is protecting an IoT device from adversaries is complex – securing an edge device is even more so. That is especially true for organizations that do not have IoT security experts within their business.
However, working with the right partners and utilizing security frameworks will enable us to build the right level of protection into our devices, which in turn means our customers can take advantage of the opportunities that digitization offers them without putting their assets at risk.
There are many security standard initiatives in the industry, but we were drawn to PSA Certified due to its composition formula. The composition formula was compelling to us, as it had separate certifications for chip, software and device, which means our certifications can be reused and reduce the work needed by the OEMs.
In 2021, we announced that our ReliaGATE 10-14 IoT edge gateway for industrial and lightly rugged applications and our IoT edge framework, Everyware Software Framework (ESF), had achieved PSA Certified Level 1 certification. We then used the certification we achieved through PSA Certified as a launchpad to meet the IEC 62443-4 series of cybersecurity standards for industrial and control systems.
Security cannot be an afterthought. It must be considered during design. What helps tremendously is to follow and build against proven security standards and frameworks.
Together, they have enabled us to show our customers that we have the necessary technical skills and that we have applied them as part of a secure development process to secure our products throughout their life cycle. They also helped us breakdown security into quantifiable elements and gave us a common language that we can use to communicate with our customers about the importance of security, their security requirements, and how our solutions align with them. We can also have a conversation about the value certification adds.

Reducing Fragmentation Within the Industry
This common language will also help us reduce fragmentation within the industry. We understand the hurdles that companies face when they are implementing security in embedded devices and in an operational technology environment. There are different architectures, protocols, and deployment scenarios. Even in networking, we must bridge different technologies, from cellular to Wi-Fi, LoRaWAN® networks, and the internet.
When we were going through the process internally, we had champions that understood the challenges and used the specifications and documentation that partnerships like PSA Certified and standards such as IEC 62443 provide. We gathered our ideas around these frameworks, and then aligned our product development with their principles.
The Value of Collaboration
It is also important to remember that security extends beyond the engineering team. The quality, production, validation, and product management teams must also be involved – it is not just a technical problem. We need a 360-degree view of security.
We also believe in working with partners across the entire edge and IoT stack to break down barriers, reduce fragmentation and improve security standards. If there are standard processes that we can adopt, it will give us confidence as an industry. It will raise the state- of-the-art to a new level and that will give us a solid foundation to build the next innovations on.
Getting Started with Security
So, where do we start?
As I have outlined here, there are frameworks and examples of industry best practice that help developers and manufacturers design security into devices. There are also pre-certified components to build on and certifications that can be re-used, such as the PSA Certified ReliaGATE 10-14 IoT edge gateway. They are a great way to start addressing the security challenges and they help breakdown security into smaller pieces, so we have a good place to begin our journey.
You can hear me discuss the security of edge devices in more detail in the PSA Certified Beyond the Now podcast. Or for more information on our PSA Certified components or other hardware, software, and integrated hardware and software solutions please visit Eurotech’s website.
