As part of Cybersecurity Awareness Month, we’re highlighting six steps you should take to #becybersmart with IoT security and help build trust in connected devices.
Cybercriminals operate in a world that is hidden from view, but they make a tangible impact. The damage bill from their activities is expected to reach a staggering $10.5 trillion annually by 2025 and it is not just the financial costs that add up. Cyberattacks put people, organizations, assets, and critical infrastructure at risk.
It is predicted that by 2025 there will be around 75.44 billion connected devices, each bringing with them new levels of service and efficiency, as well as unlocking new business models and revenue streams. However, in order to realize the potential of the Internet of Things (IoT) and digital transformation, the data driving this new reality has to be trusted. Trusted data can only come from trusted devices.
In October, as part of our support for Cybersecurity Awareness Month, we are highlighting the importance of securing the IoT. To help device makers, we are simplifying security by outlining the six steps you should take to protect your device from the most common attacks. That is, we are helping you to #BeCyberSmart. Importantly, the best practice we are sharing is quick, easy, and cost-effective to implement.

Step 1: Design Security into Your Device, Starting at the Silicon
Secure by design is an approach to software and hardware development that means security is implemented from the outset, rather than in response to a cyberattack. It requires you to think like an attacker and layer your defenses in a way that protects the device and the data, even in the event of a security breach. In practice, that means starting with the silicon, and moving through to the system software and endpoint device.
It becomes increasingly important to build security in from the ground up when the number of IoT devices being shipped continues to grow because a vulnerability in a single product can bring down an entire system. In the past, security was often an afterthought because companies were racing to get their products to market. This led to serious security breaches because it is not easy to retrofit IoT security, as Jan Munther, Head of Digital Product Security at ams OSRAM, explains: “Instead of just testing the security of a product after it has been developed, I think it’s enormously important to already get a foot in the door in the requirements engineering phase, in the design and architecture phase.”

Step 2: Follow an IoT Security Framework to Reduce Costs and Complexity
An easy-to-use framework will make building security into your device from the outset quicker, more affordable, and more straightforward. There are comprehensive and free resources that have been developed to help device makers, and they enable you to meet basic security requirements, even if you do not have access to dedicated expertise.
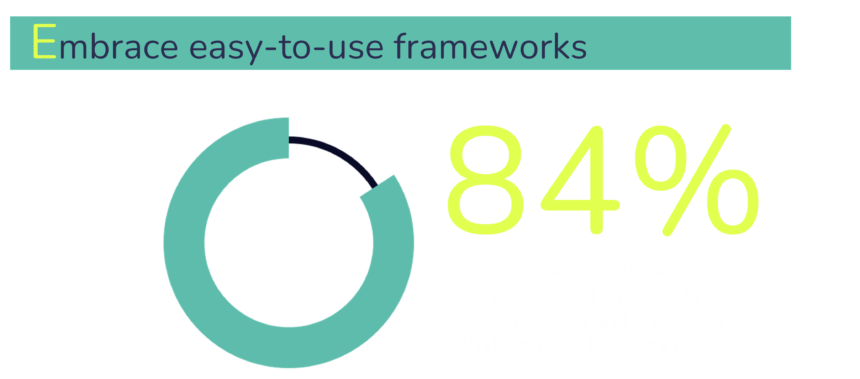
Eighty-four percent of the tech decision-makers that responded to the PSA Certified Security Report 2021 said they were interested in an industry-led set of guidelines and processes to help them build security into their devices. Security frameworks respond to that demand and unite the ecosystem through a common language as well as standardize security across the value chain. Some also align with major global standards and regulations, which makes it easier to navigate the ever-changing compliance landscape, especially if you ship your products globally.
Step 3: Identify the Threats to Your Device using Threat Modeling
Threat modeling is the process of identifying the assets that need to be protected (including data) and the potential threats to your device. It helps you determine what you need to do to safeguard your technology from potential adversaries and ultimately, keep your device and its data secure. As Anoop Nair, Senior Director, Software CTO Group, Flex, says: “The more devices you have, the more openings you provide for hackers – that’s the challenge. We have to close all the gaps. A hacker only has to look for the weakest link.”
Threat modeling is conducted at the beginning of the design process and enables you to design right-size security. That is, implement the right level of security for your device and use case, rather than investing time and money in measures you do not need. It is relevant for businesses of all sizes, even the smallest firms, where our research suggests that only a third are following best practices by carrying out a threat analysis every time they design new products.
Step 4: Benefit from the Expertise Within the Ecosystem by Utilizing Trusted Components
The PSA Certified 2021 Security Report found an overwhelming desire from the industry for better collaboration with 85% of tech decision-makers interested in better cross-market knowledge sharing around IoT security. This is important as a lot of hard work has already been done by security experts within the ecosystem, that can be leveraged by all members of the value chain, reducing the need for specific expertise.
Some silicon providers and software developers have created products that have been assessed and certified as being secure. You can use these components to create a firm foundation to build your own products on. As Christophe Mani, STM32 Ecosystem Security Marketing Manager at STMicroelectronics says: “Device manufacturers can offer consumer products that are less impacted by price and can innovate quickly without the heavy burden of specialized engineering expertise.” Using certified components will also help you reduce the total cost of ownership because security has already been built-in, as well as helping you build trust in your product.
Step 5: Reduce Risk and Increase Assurance
Connected technologies are transforming industries by enabling new products and services to be created. However, the challenge is that the scale and pace of change are unprecedented. That means it is difficult for industry observers, including insurers, to understand the risks involved in developing an IoT device, and if an insurer cannot quantify the risk and know who is liable if something goes wrong, they cannot support the rollout of new technologies. That will stifle innovation and slow deployment.
So, to help build their trust in the IoT, we must all play our part in making it more secure. We can do that by utilizing frameworks that are built on industry best practices and are aligned with major global regulations and standards. We can also use trusted components such as a Root of Trust to establish a foundation of security, which will give insurers the confidence that we have put cybersecurity first. Peter Armstrong, Senior Cyber Subject Matter Expert at the world-leading insurer, Munich Re, explains further: “The defined Root of Trust protocols that talk to nuanced issues can provide confidence and an easy win for insurers. It can speed up adoption and deployment of the new technologies because we can offer warranties to back those technologies.”

Step 6: Demonstrate your Commitment to Security with Third-party Evaluation and Certification
According to our Security Report, almost two-thirds (62%) of companies verify their security implementation internally, and that suggests there are different approaches to security and several propriety solutions. Customers and industry will benefit if all manufacturers are being assessed against the same security criteria.
Third-party evaluation helps you assure your customers that your device has been designed in accordance with security best practices and that it aligns to major global standards and regulations. It moves you away from saying ‘trust me, my device is secure’ to being able to demonstrate that your implementation has been assessed by independent security experts. For the wider industry, third-party evaluation and certification also standardize security, providing an essential mechanism to build trust in the IoT.
Security certification means customers can make informed decisions about the level of protection they want in a device. It also enables you to differentiate yourself from competitors that have not invested in improving the security of their products. Mike Dow, Senior Product Manager for IoT Security at Silicon Labs states: “Customers will find it difficult to understand the inner workings of security architectures, but what they can understand is a security standard and label – this is why security certifications like PSA Certified are needed.”

How PSA Certified Can Help
PSA Certified is a global partnership offering a security framework and independent evaluation that demonstrates commitment to security best practice. The certification scheme provides a comprehensive and accessible approach to lab-verified, secure design, that aligns to worldwide security requirements and unites the ecosystem under a common language. Supported by a comprehensive set of free resources, PSA Certified and its growing ecosystem of certified silicon. system software and end devices are democratizing security access and giving the electronics industry the confidence to create.
To simplify security even further, here is a handy checklist and summary of the six steps we just discussed:

Read the PSA Certified 2021 Security Report
Discover more about IoT security challenges and how we can collaborate on the solutions in the PSA Certified 2021 Security Report.
